Die Rolle des Datenschutzes bei der Abmilderung der Risiken des Salz-Taifuns für Dritte
Die jüngsten Enthüllungen über den massiven Cyberangriff von Salt Typhoon auf die globalen Telekommunikationsnetze führen uns eindringlich vor Augen, dass sich Cyberbedrohungen immer weiter entwickeln und immer raffinierter werden. Während sich die Angreifer darauf konzentrierten, die Kommunikation abzufangen und sensible Daten zu exfiltrieren, werfen ihre Aktionen ein Schlaglicht auf ein breiteres, dringlicheres Problem: die Unzulänglichkeit herkömmlicher Datenschutzmethoden beim Schutz kritischer Infrastrukturen.
Wir bei HYCU sind der Meinung, dass dieses Ereignis ein dringender Handlungsaufruf für Unternehmen ist, ihre Herangehensweise an Cyber-Resilienz mit Backup und Wiederherstellung zu überdenken. Lassen Sie uns die Lehren aus diesem Angriff ziehen und untersuchen, wie die Lösungen von HYCU den wachsenden Schwachstellen in einer hypervernetzten, SaaS-abhängigen Welt begegnen.
Die Anatomie des Salt Typhoon-Angriffs
Die chinesische Hacking-Kampagne mit dem Namen Salt Typhoon ist eine der größten Sicherheitsverletzungen der Geschichte. Nach Angaben der US-Regierung ist die Kampagne zwar noch nicht abgeschlossen, aber es wurden bereits acht US-amerikanische Telekommunikations- und Internet-Provider sowie Dutzende von anderen weltweit angegriffen. Salt Typhoon ist eine der größten nachrichtendienstlichen Kompromittierungen in der Geschichte der USA und zielt auf Schwachstellen bei Telekommunikationsanbietern ab, wobei Schwachstellen in der Netzwerkinfrastruktur ausgenutzt werden, um dauerhaften Zugang zu erhalten. Der Ansatz der Hacker ermöglichte die langfristige Überwachung der Kommunikation und die Exfiltration hochsensibler Daten.
Diese Art von Advanced Persistent Threat (APT) gedeiht auf schwachen Erkennungssystemen, unzureichend geschützten Datenbeständen und unzureichenden Wiederherstellungsmechanismen. Für Telekommunikationsunternehmen gefährden Cyberangriffe und Datenschutzverletzungen dieses Ausmaßes Millionen von Kunden und die nationale Sicherheit.
Angriffe auf die Lieferkette: Die wahren Kosten des Risikos von Drittanbietern verstehen
Durch die Kompromittierung eines einzigen Anbieters in der Lieferkette können Angreifer Tausende von Unternehmen in der Folge erreichen. Aufsehen erregende Vorfälle wie der Salt Typhoon-Angriff, der Snowflake-Angriff, Massenlöschungen in öffentlichen Cloud-Umgebungen und der CrowdStrike-Angriff zeigen, wie massiv dieses Risiko geworden ist.
Ein einziger Sicherheitsverstoß bedroht nicht nur ein Unternehmen, sondern kann sich auf ganze Branchen ausbreiten und sich auf jeden Kunden auswirken, der in Bezug auf Umsatz, Compliance und Vertrauen auf den kompromittierten Dienst angewiesen ist.
Wiederherstellung als letzte Verteidigungslinie
Cloud-Plattformen bieten einen enormen Wert, aber die Komplexität der heutigen IT-Infrastruktur bedeutet, dass Sie und Ihr Team oft auf Hunderte von SaaS-Anwendungen angewiesen sind - jede ein potenzieller Einstiegspunkt für Angreifer. Selbst bekannte Lösungen wie LastPass oder Typeform haben sich als anfällig erwiesen. Dies unterstreicht, wie wichtig es ist, nicht nur Ihre Daten zu sichern, sondern auch zu wissen, wie Sie sie schnell wiederherstellen können, wenn das Unerwartete eintritt.
Das Modell der geteilten Verantwortung: Mehr als nur Infrastruktur
Die rasche Einführung von SaaS-Plattformen hat die Arbeitsweise von Unternehmen verändert und bietet Skalierbarkeit, Flexibilität und geringere Infrastrukturkosten. Der Angriff auf Salt Typhoon unterstreicht jedoch, wie viele andere auch, die Notwendigkeit, dass die Kunden ihre Verantwortung verstehen.
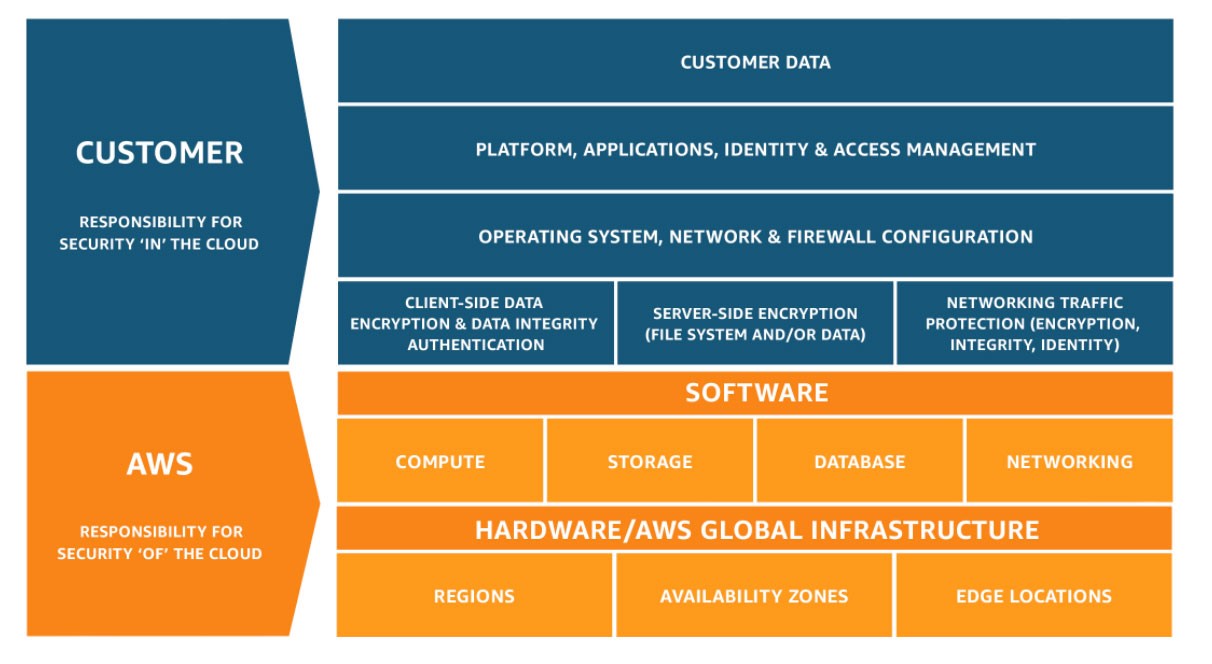
Shared Responsibility Model
Während Cloud- und SaaS-Anbieter hart daran arbeiten, die Betriebszeit und die Sicherheit der Infrastruktur zu gewährleisten, Der Schutz der eigentlichen Daten liegt immer noch bei Ihnen. Das ist ein häufiges Missverständnis: Viele Unternehmen gehen davon aus, dass ihre SaaS-Daten automatisch gesichert und wiederherstellbar sind. In Wirklichkeit ist es nicht die Aufgabe des Anbieters, einen wichtigen Datensatz wiederherzustellen, wenn jemand aus Ihrem Team diesen löscht - es ist Ihre Aufgabe.
Auch wenn Anbieter ihre eigenen Operationen nach einem Angriff oder einer Sicherheitsverletzung wiederherstellen, ist es für Sie am besten, immer eine sichere, ausgelagerte Kopie Ihrer Daten zu haben. Wenn etwas schief geht, müssen Sie nicht darauf warten, dass jemand anderes Ihre Daten wiederherstellt.
Hier kommt HYCU ins Spiel.
HYCU's einzigartiger Ansatz für Backup und Wiederherstellung
Wir bei HYCU haben uns darauf spezialisiert, maßgeschneiderte Backup- und Wiederherstellungslösungen anzubieten, die sicher und einfach für Unternehmen sind. Ganz gleich, ob Ihre Daten in der Cloud, vor Ort oder auf SaaS-Plattformen wie Microsoft 365 gespeichert sind, Google Workspace, Salesforce, oder GitHub, stellen wir sicher, dass Ihre kritischen Informationen geschützt und wiederherstellbar sind, egal was passiert.
Unser Ansatz beruht auf drei Säulen:
- Vollständige Sichtbarkeit mit R-Graph:
HYCU R-Graph lässt Sie jede Anwendung und jeden Dienst, den Sie nutzen, in einer einzigen Ansicht sehen. Sie können schnell erkennen, welche kritischen Anwendungen derzeit nicht geschützt oder wiederherstellbar sind, so dass Sie diese Lücken schließen können, bevor sie zu Problemen werden. - Automatisierte, sichere Backups:
Mit nur wenigen Klicks im HYCU Marketplace können Sie jede Anwendung schützen und automatische Backup-Richtlinien festlegen, die rund um die Uhr funktionieren. Ihre Backups werden außerhalb der ursprünglichen Cloud- oder SaaS-Umgebung auf kundeneigenem, WORM-fähigem Speicher gespeichert, was maximale Sicherheit gewährleistet. - Schnelle Wiederherstellung mit einem Klick:
Bei einem Angriff oder einer versehentlichen Löschung ermöglicht HYCU eine schnelle Wiederherstellung mit nur einem Klick - ganz gleich, ob Sie ganze Datensätze oder eine einzelne Datei wiederherstellen müssen. Da Ihre Backups ausgelagert und sicher sind, können Sie Ausfallzeiten minimieren und Ihren Betrieb reibungslos aufrechterhalten.
Warum Telekommunikationsanbieter und ISPs eine neue Perspektive für den Datenschutz brauchen
Für Telekommunikationsanbieter und ISPs sind Daten mehr als nur ein Vermögenswert - sie sind das Lebenselixier des Betriebs. Der Angriff auf Salt Typhoon unterstreicht die Bedeutung einer mehrschichtigen Datenschutzstrategie, die Folgendes umfasst:
- Reguläre, unveränderliche Backups: Verhindern Sie, dass Angreifer Ihre Backup-Dateien manipulieren oder verschlüsseln.
- Automatisierte Wiederherstellungstests: Stellen Sie sicher, dass Backups nicht nur vollständig, sondern auch in einem realen Szenario wiederherstellbar sind.
- Umfassende Abdeckung: Schützen Sie Daten in hybriden, Multi-Cloud-Umgebungen, einschließlich SaaS-Anwendungen, um die Lücken in Ihrer Strategie zu schließen.
Proaktive Schritte für einen widerstandsfähigen Datenschutz
Um Ihre Daten während eines Angriffs auf die Lieferkette sicher und zugänglich zu halten, empfiehlt HYCU diese proaktiven Schritte:
- Kartografieren Sie Ihren gesamten Datenbestand: Identifizieren Sie alle Cloud-basierten Dienste und Anwendungen außerhalb Ihres Rechenzentrums und stellen Sie sicher, dass Sie für jede einzelne ein zuverlässiges Backup und Wiederherstellungspläne haben.
- Schützen Sie Ihre IAM-Konfigurationen: Angreifer nutzen häufig privilegierte Konten aus. Indem Sie Ihre Einstellungen für die Identitäts- und Zugriffsverwaltung (IAM) von einem sicheren Zeitpunkt aus sichern und wiederherstellen, können Sie unbefugten Zugriff schnell unterbinden.
- Unabhängige Offsite-Backups erstellen: Speichern Sie Backups an einem Ort, den nur Sie kontrollieren. Befolgen Sie die 3-2-1-Regel (drei Kopien, zwei Medientypen, eine außer Haus), um sicherzustellen, dass Sie immer einen sicheren Rückgriff haben.
- Verwenden Sie unveränderliche Backups: Stellen Sie sicher, dass Ihre Backups WORM-fähig sind und an einem externen Standort gespeichert werden. Dadurch sind sie vor Ransomware und anderen Bedrohungen geschützt, so dass Ihre Wiederherstellung intakt bleibt.
- Erstellen und Testen von Plänen zur Reaktion auf Vorfälle: Entwickeln Sie eine klare, dokumentierte Strategie für den Umgang mit Verstößen Dritter. Beziehen Sie interne Teams, Anbieter und Aufsichtsbehörden mit ein und testen Sie die Strategie regelmäßig, damit jeder seine Rolle kennt, wenn es darauf ankommt.
Wie HYCU helfen kann
Als führendes Unternehmen im Bereich Multi-Cloud- und SaaS-Datenschutz ermöglicht HYCU Unternehmen, ihre Daten zu schützen, egal wo sie sich befinden. Mit unseren Lösungen können Sie:
- Compliance vereinfachen: Erfüllen Sie regulatorische Anforderungen mit minimaler Komplexität.
- Minimieren Sie Ausfallzeiten und Datenverluste: Stellen Sie die Betriebskontinuität sicher, selbst bei einem Sicherheitsverstoß.
- Sichern Sie SaaS-Anwendungen: Schützen Sie Daten, die auf führenden SaaS-Plattformen gespeichert sind, ohne sich ausschließlich auf die nativen Wiederherstellungsoptionen zu verlassen.
Salt Typhoon mag ein Weckruf sein, aber er ist auch eine Gelegenheit, Ihre Verteidigung zu stärken und Ihr Unternehmen zukunftssicher gegen neue Bedrohungen zu machen. Mit HYCU haben Sie die Gewissheit, dass Ihre Daten immer geschützt, immer wiederherstellbar und immer sicher sind.
Abschluss: Aufbau einer sichereren digitalen Zukunft
Der Salt Typhoon-Angriff hat Schwachstellen im Telekommunikations- und ISP-Sektor aufgedeckt, aber die daraus gezogenen Lehren gehen weit über eine einzelne Branche hinaus. Egal, ob Sie ein Telekommunikationsunternehmen, ein ISP, ein SaaS-abhängiges Unternehmen oder ein Multi-Cloud-Unternehmen sind, Datenschutz muss für alle oberste Priorität haben.
Wir bei HYCU haben uns verpflichtet, Unternehmen bei der Bewältigung dieser Herausforderungen mit Lösungen zu unterstützen, die speziell für moderne Anforderungen entwickelt wurden. Gemeinsam können wir eine sicherere und widerstandsfähigere digitale Zukunft schaffen.
Beginnen Sie noch heute mit HYCU
Möchten Sie sehen, wie HYCU Ihren Ansatz zum Datenschutz verändern kann? Beginnen Sie mit einer 14-tägigen kostenlosen Testversion oder fordern Sie eine persönliche Demo an, um unsere auf Ihre Bedürfnisse zugeschnittenen Lösungen kennenzulernen.
👉 Melden Sie sich hier für eine Demo an
Zusätzliche Ressourcen
- HYCU als Marktführer und Schnelldreher im GigaOm Sonar for Cloud-Native Data Protection Report
- The State of SaaS Data Resilience in 2024
- Gartner Magic Quadrant for Enterprise Backup and Recovery: Sehen Sie, warum HYCU bereits drei Jahre in Folge als Visionär ausgezeichnet wurde.
- Datensicherheit von SaaS mit geteilter Verantwortung in der Cloud
