What is the Digital Operational Resilience Act (DORA)?
The Digital Operational Resilience Act (DORA) is a regulation set to transform digital risk management in the European Union's (EU) financial industry. Essentially, DORA is a set of requirements for EU financial institutions to protect their key business processes from technology risks and reshape how they approach digital risk, incident management, and third-party relationships.
Specifically, DORA aims to strengthen the IT security of banks, insurance companies, investment firms, and other financial sector organizations.
For EU finance companies, the spotlight is on IT Directors and C-suite executives to understand and prepare for DORA as not just a regulatory requirement—but as a strategic imperative. This urgency is underscored by the severe consequences of non-compliance:
- Financial Penalties: Fines of up to €10 million and for severe or repeated violations, these fines can be doubled.
- Damage of Consumer Trust: Non-compliance can lead to increased vulnerability to cyber incidents, potentially resulting in data breaches or service disruptions. These events can damage an organization reputation, affect consumer confidence, and lead to customer churn and decreased market share.
- Personal Criminal Liability: In cases of severe negligence or willful misconduct, senior management and board members may face personal criminal liability. This could include individual fines, professional disqualification, and even imprisonment in extreme cases. This personal risk emphasizes the need for top-level engagement in ensuring DORA compliance.
Given these high stakes, the spotlight is on IT Directors and C-suite executives to understand and prepare for DORA as not just a regulatory requirement—but as a strategic imperative.
Background and History
ICT-related incidents within financial institutions have the potential to cause significant disruptions, financial losses, and reputational damage.
DORA is a key component of the European Commission's broader digital finance strategy.
It aims to:
- Consolidate and upgrade ICT risk requirements within the financial sector
- Establish a framework for ICT providers, including cloud platforms
- Create a mechanism for incident reporting to increase awareness of cyber threats
- Strengthen digital operational resilience testing
By creating consistency, these requirements across the EU, DORA will help to enhance the overall stability and integrity of financial systems.
Why DORA is Important
DORA represents a significant shift in creating a uniform approach to ICT risk management across the EU financial sector. It addresses the growing concerns about cyber threats and technological vulnerabilities that could potentially disrupt the financial industry.
Key aspects include:
- Comprehensive scope: DORA applies to a wide range of financial entities, including banks, insurance companies, investment firms, and financial service providers.
- Harmonization: It establishes consistent ICT risk management requirements across the EU, replacing the current patchwork of national regulations.
- Third-party oversight: DORA introduces a framework for overseeing critical ICT third-party service providers, including cloud services.
- Incident reporting: It mandates standardized reporting mechanisms for major ICT-related incidents.
- Resilience testing: DORA requires regular testing of digital operational resilience.
Key Areas of DORA
1. ICT risk management
DORA mandates a comprehensive ICT risk management framework. This includes:
- Identifying and documenting ICT-related business functions, resources, and dependencies
- Continuous risk assessment and mitigation strategies
- Implementing protection and prevention measures
- Developing detection capabilities
- Establishing response and recovery procedures
2. Incident reporting
Implementing processes to monitor and log ICT incidents. They are required to classify these incidents using criteria specified by DORA. Additionally, they must report major incidents to relevant authorities within strict timeframes.
3. Response and recovery
Significant emphasis on response and recovery capabilities include -
Incident Response Plans:
- Develop, document, and implement comprehensive plans to respond to and recover from ICT-related incidents.
- These plans should detail procedures for prompt incident detection, analysis, containment, and mitigation.
Business Continuity:
- Maintain a business continuity policies and disaster recovery plans.
- Regular testing of these plans is mandatory to ensure effectiveness.
Backup Procedures:
- DORA mandates regular backups of critical systems and data.
- Specific requirements include defined backup frequency, secure off-site storage, and regular testing of backup restoration processes.
Recovery Time Objectives (RTOs):
- Establish and regularly test the ability to restore systems within defined time frames.
- Minimize operational disruptions and ensure rapid recovery from incidents.
Communication Protocols:
- Clear procedures for internal and external communication during incidents must be established.
- Ensure timely and effective response, including notification to relevant authorities and stakeholders.
Post-Incident Analysis:
- After significant incidents, organizations must conduct thorough root cause analyses.
- Lessons learned should be incorporated into improving risk management frameworks.
4. Digital operational resilience testing
DORA introduces a harmonized framework for testing digital operational resilience:
- Basic testing such as vulnerability assessments and network security scans for all entities
- Advanced testing, including threat-led penetration testing (TLPT) for significant entities
5. ICT Third-Party Risk Management
With the increased reliance on third-party service providers, DORA creates:
- Principles to be included in agreements with ICT third-party service providers
- A new oversight framework for critical ICT third-party service providers

Source: McKinsey
6. Information Sharing
The exchange of cyber threat information and intelligence among financial entities to enhance collective resilience.
Scope and Application
DORA applies to a wide range of financial entities operating in the EU, including:
- Credit institutions
- Payment institutions
- Electronic money institutions
- Investment firms
- Trading venues
- Insurance and reinsurance undertakings
- Credit rating agencies
- Statutory auditors and audit firms
- Administrators of critical benchmarks
- Account information service providers
- Crypto-asset service providers
- Central securities depositories
- Data reporting service providers
- Third party service providers
Actions for Compliance
To meet DORA's requirements, CIOs, CTOs, IT Directors, and other key IT individuals should focus on the following actions:
- Assess current frameworks: Evaluate existing ICT risk management processes against the requirements to identify gaps.
- Enhance ICT risk management: Implement processes for identifying, protecting against, detecting, responding to, and recovering from ICT-related disruptions.
- Develop incident reporting mechanisms: Establish systems and procedures to detect and report major ICT-related incidents within required timeframes.
- Conduct resilience testing: Implement a program of regular resilience testing, including vulnerability assessments and penetration testing.
- Review third-party contracts: Assess and update agreements with ICT service providers to ensure they meet the requirements.
- Prepare for audits: Be ready for potential regulatory audits by maintaining comprehensive documentation of your ICT risk management practices.
- Implement business continuity and data protection measures: Develop and regularly test business continuity and disaster recovery plans, establish secure backup procedures, enhance data protection, create crisis communication protocols, and conduct staff training as per Articles 10 and 11 requirements.
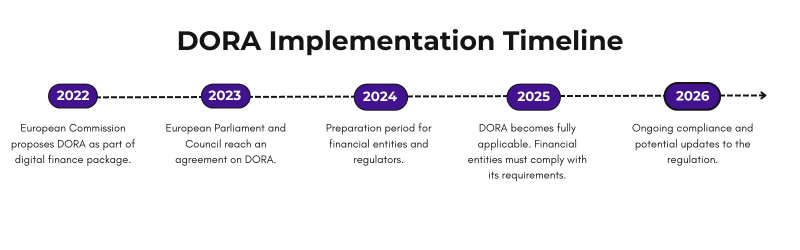
Deadlines and Compliance
DORA entered into force on January 16, 2023. However, financial entities have until January 17, 2025, to ensure full compliance. This two-year window is crucial for organizations to assess their current systems, implement necessary changes, and prepare for the new regulatory environment.
The Importance of Acting Now
While 2025 may seem distant, the scope and depth of changes required by DORA necessitate early action. Begin preparing now will be better positioned to:
- Spread the cost of compliance over a longer period
- Gain a competitive advantage by demonstrating strong digital resilience
- Avoid last-minute rushes and potential non-compliance penalties
- Contribute to the overall stability and trustworthiness of the EU financial system
Further information
